Video Here: https://youtu.be/olna19zwtoE?si=K-PJgKt6HW8Q0HJ_
When starting a homelab I’ve seen way too many posts on Reddit and other forums about “how can I host ‘xyz’ website” or “how can I expose ‘abc’ services so my friends can watch my lifes worth of ‘family’ movies”. But people quickly find themselves in trouble because they didn’t take #cybersecurity into account first to ensure their system is up to par to even host these services.
While most will say “use a VPN to a VPS” or “use Cloudflare tunnels” or “only open 80/443” all of which is OK (sorta), you are only as secure as your weakest link. If your web server (be it a VM or dedicated hardware) has unpatched vulnerabilities, you have now potentially exposed those vulnerabilities to the web for everyone to see.
At the bare minimum, companies such as Tenable, Greenbone (OpenVAS) or Qualys are offering free vulnerability scanners for your network that you can install and configure. While my career has been been deep into the Nessus/ACAS suite of tools, I’ve recently toyed with Qualys and was quite impressed with their hybrid cloud model of vulnerability scanning (which at the time of this writing offers 3 external ip’s and 16 LAN ip’s to be scanned).
Using a vulnerability scanner provides a ton of insight of vulnerabilities and remediation’s to fix them. Below are some examples from Tenable Essentials (free for up to 16 IP’s).
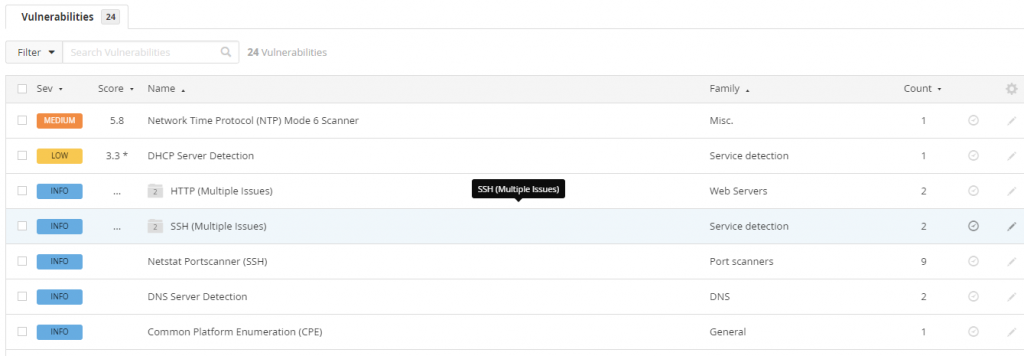
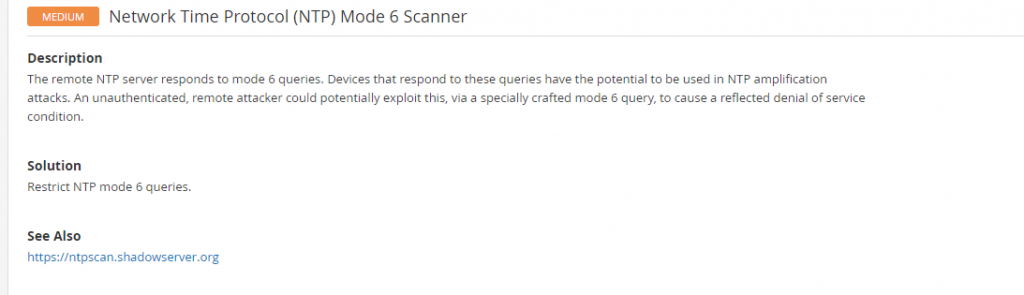
When you click into each vulnerability you get detailed information regarding them, including the fix:
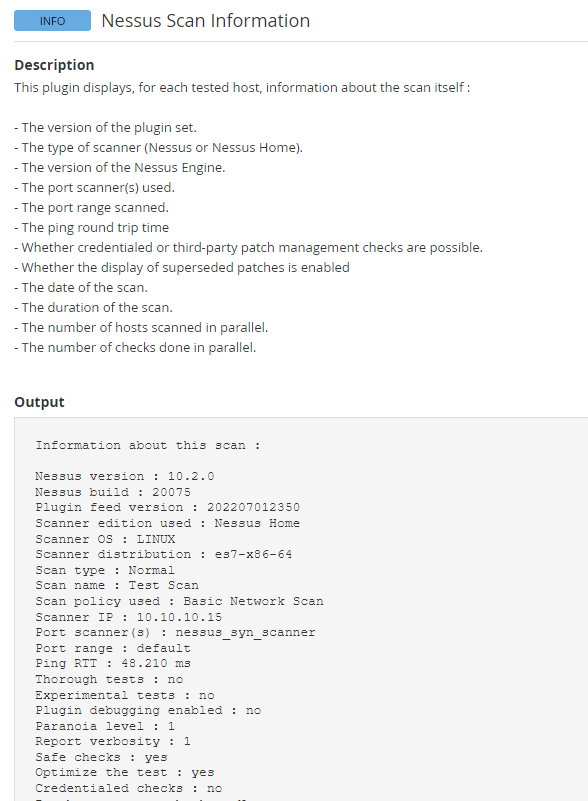
Just ensure that when you set up your vulnerability scanner, that you are getting good credentialed scans (for Tenable/Nessus/ACAS look at plugin 19506), otherwise you will receive incomplete results. The vulnerability scanners need to have credentialed and elevated privileges in order to understand the contents of each systems patch level, security posture, network settings, etc., (think of what an intruder/hacker would see if they got in) in order to tell you what to remediate/fix.
Not only will this help you keep a better security posture for your network and internal infrastructure, in the future if you decide to step into the world of Information Technology/Cybersecurity this can be used as experience. In previous interviews, I’ve impressed recruiters/hiring managers by telling them “I run a #homelab with a vulnerability scanner in the middle scanning all of my network devices on a weekly basis”. That opens the door to further conversations where I can deep dive into what I’ve done and my experience in how I use this to ensure my network, devices, and computers are safe.
